[toc]
kubernetes 操作记录四
kubernetes认证及Service Account
在master服务器上启动 proxy 并监听至8080
# kubectl proxy --port=8080 &
# curl http://localhost:8080/api/v1/namespaces
仅有权限获取当前Pod自身的相关信息
# kubectl get secret -n ingress-nginx
NAME TYPE DATA AGE
default-token-t54dl kubernetes.io/service-account-token 3 5d23h
nginx-ingress-serviceaccount-token-5dwv4 kubernetes.io/service-account-token 3 5d23h
生成yaml框架,快速编写清单
# kubectl create serviceaccount mysa -o yaml --dry-run
apiVersion: v1
kind: ServiceAccount
metadata:
creationTimestamp: null
name: mysa
# kubectl get pods myapp-deploy-675558bfc5-2rfrs -o yaml --export
# kubectl create serviceaccount admin
# kubectl describe sa admin
Name: admin
Namespace: default
Labels: <none>
Annotations: <none>
Image pull secrets: <none>
Mountable secrets: admin-token-hxqqf
Tokens: admin-token-hxqqf
Events: <none>
# kubectl get secret
NAME TYPE DATA AGE
admin-token-hxqqf kubernetes.io/service-account-token 3 66s
default-token-2sgn5 kubernetes.io/service-account-token 3 26d
mysql-root-password Opaque 1 45h
tomcat-ingress-secret kubernetes.io/tls 2 5d22h
# vim pod-sa-demo.yaml
apiVersion: v1
kind: Pod
metadata:
name: pod-sa-demo
namespace: default
labels:
app: myapp
tier: frontend
annotations:
ssjinyao.com/create-by: "cluster admin"
spec:
containers:
- name: myapp
image: ikubernetes/myapp:v1
ports:
- name: http
containerPort: 80
serviceAccountName: admin
# kubectl apply -f pod-sa-demo.yaml
# kubectl describe pods pod-sa-demo | grep 'SecretName'
SecretName: admin-token-hxqqf
kubernetes 集群有两类认证时的用户账号
useraccount,我们称之为用户账号,通常定义的是人使用的账号
servicecacount, 服务账号,指pod中应用的应用程序运行在kubernetes ,想访问apiserver时用的认证信息,包括用户名密码等等;
# kubectl config view
apiVersion: v1
clusters:
- cluster:
certificate-authority-data: DATA+OMITTED
server: https://10.1.87.80:6443
name: kubernetes
contexts:
- context:
cluster: kubernetes
user: kubernetes-admin
name: kubernetes-admin@kubernetes
current-context: kubernetes-admin@kubernetes
kind: Config
preferences: {}
users:
- name: kubernetes-admin
user:
client-certificate-data: REDACTED
client-key-data: REDACTED
/etc/kubernetes/pki
# (umask 077; openssl genrsa -out ssjinyao.key 2048)
# openssl req -new -key ssjinyao.key -out ssjinyao.csr -subj "/CN=ssjinyao"
# openssl x509 -req -in ssjinyao.csr -CA ca.crt -CAkey ca.key -CAcreateserial -out ssjinyao.crt -days 36500
Signature ok
subject=/CN=ssjinyao
Getting CA Private Key
# openssl x509 -in ssjinyao.crt -text -noout
Certificate:
Data:
Version: 1 (0x0)
Serial Number:
f3:fe:ff:e5:0e:0b:37:e2
Signature Algorithm: sha256WithRSAEncryption
Issuer: CN=kubernetes
Validity
Not Before: May 22 07:57:01 2019 GMT
Not After : Apr 28 07:57:01 2119 GMT
Subject: CN=ssjinyao
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (2048 bit)
接下来把用户账号信息添加到连接kubernetes 的配置信息
# kubectl config set-credentials ssjinyao --client-certificate=./ssjinyao.crt --client-key=./ssjinyao.key --embed-certs=true
User "ssjinyao" set.
# kubectl config view
apiVersion: v1
clusters:
- cluster:
certificate-authority-data: DATA+OMITTED
server: https://10.1.87.80:6443
name: kubernetes
contexts:
- context:
cluster: kubernetes
user: kubernetes-admin
name: kubernetes-admin@kubernetes
current-context: kubernetes-admin@kubernetes
kind: Config
preferences: {}
users:
- name: kubernetes-admin
user:
client-certificate-data: REDACTED
client-key-data: REDACTED
- name: ssjinyao
user:
client-certificate: /etc/kubernetes/pki/ssjinyao.crt
client-key: /etc/kubernetes/pki/ssjinyao.key
# kubectl config set-context ssjinyao@kubernetes --cluster=kueberntes --user=ssjinyao
Context "ssjinyao@kubernetes" created.
# kubectl config view
apiVersion: v1
clusters:
- cluster:
certificate-authority-data: DATA+OMITTED
server: https://10.1.87.80:6443
name: kubernetes
contexts:
- context:
cluster: kubernetes
user: kubernetes-admin
name: kubernetes-admin@kubernetes
- context:
cluster: kueberntes
user: ssjinyao
name: ssjinyao@kubernetes
current-context: kubernetes-admin@kubernetes
kind: Config
preferences: {}
users:
- name: kubernetes-admin
user:
client-certificate-data: REDACTED
client-key-data: REDACTED
- name: ssjinyao
user:
client-certificate: /etc/kubernetes/pki/ssjinyao.crt
client-key: /etc/kubernetes/pki/ssjinyao.key
这时候多了一个context, 可切换用户
# kubectl config use-context ssjinyao@kubernetes
Switched to context "ssjinyao@kubernetes".
# kubectl config set-cluster mycluster --kubeconfig=/tmp/test.conf --server="https://10.1.87.80:6443" --certificate-authority=/etc/kubernetes/pki/ca.crt --embed-certs=true
Cluster "mycluster" set.
# kubectl config view --kubeconfig=/tmp/test.conf
apiVersion: v1
clusters:
- cluster:
certificate-authority-data: DATA+OMITTED
server: https://10.1.87.80:6443
name: mycluster
contexts: []
current-context: ""
kind: Config
preferences: {}
users: []
RBAC
授权插件: Node, ABAC,RBAC,Webhook(基于http的回调来实现)
RBAC: Role-based AC
角色 (role)
许可 (permission)
role: operations,objects
rolebinding: user account OR service account , role
clusterrole: clusterrolebinding
操作: GET HEAD PUT PUST PATCH DELETE
role binding定义
# kubectl create role pods-reader --verb=get,list,watch --resource=pods --dry-run -o yaml > role-demo.yaml
# vim role-demo.yaml
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:
creationTimestamp: null
name: pods-reader
namespace: default
rules:
- apiGroups:
- ""
resources:
- pods
verbs:
- get
- list
- watch
# kubectl apply -f role-demo.yaml
# kubectl describe role pods-reader
Name: pods-reader
Labels: <none>
Annotations: kubectl.kubernetes.io/last-applied-configuration:
{"apiVersion":"rbac.authorization.k8s.io/v1","kind":"Role","metadata":{"annotations":{},"creationTimestamp":null,"name":"pods-reader","nam...
PolicyRule:
Resources Non-Resource URLs Resource Names Verbs
--------- ----------------- -------------- -----
pods [] [] [get list watch]
# kubectl create rolebinding ssjinyao-read-pods --role=pods-reader --user=ssjinyao --dry-run -o yaml > rolebinding-demo.yaml
# vim rolebinding-demo.yaml
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
creationTimestamp: null
name: ssjinyao-read-pods
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: Role
name: pods-reader
subjects:
- apiGroup: rbac.authorization.k8s.io
kind: User
name: ssjinyao
clusterrole binding 定义
# useradd ik8s
# cp -a .kube/ /home/ik8s/
# chown -R ik8s.ik8s /home/ik8s/
#
# kubectl config use-context kubernetes-admin@kubernetes
# kubectl create clusterrole cluster-reader --verb=get,list,watch --resource=pods -o yaml --dry-run > clusterrole-demo.yaml
# vim clusterrole-demo.yaml
kind: ClusterRole
metadata:
name: cluster-reader
rules:
- apiGroups:
- ""
resources:
- pods
verbs:
- get
- list
- watch
# kubectl apply -f clusterrole-demo.yaml
clusterrole.rbac.authorization.k8s.io/cluster-reader created
# kubectl create clusterrolebinding ssjinyao-read-all-pods --clusterrole=cluster-reader --user=ssjinyao --dry-run -o yaml > clusterrolebind-demo.yaml
cluster-role 被 rolebinding 会使的cluster 被降级
# kubectl create rolebinding ssjinyao-read-pods --clusterrole=cluster-reader --user=ssjinayo --dry-run -o yaml > rolebinding-clusterrole-demo.yaml
查看系统默认的授权
引用授权
# kubectl get clusterrole admin -o yaml
# kubectl create rolebinding default-ns-admin --clusterrole=admin --user=ssjinyao
rolebinding.rbac.authorization.k8s.io/default-ns-admin created
dashboard 及认证分级授权
部署 dashboard
# kubectl apply -f https://raw.githubusercontent.com/kubernetes/dashboard/v1.10.1/src/deploy/recommended/kubernetes-dashboard.yaml
部署时下载镜像出错
# kubectl describe pods -n kube-system kubernetes-dashboard-5f7b999d65-jpmhs
Events:
Type Reason Age From Message
---- ------ ---- ---- -------
Normal Scheduled 113s default-scheduler Successfully assigned kube-system/kubernetes-dashboard-5f7b999d65-jpmhs to node01
Warning Failed 53s (x3 over 105s) kubelet, node01 Failed to pull image "k8s.gcr.io/kubernetes-dashboard-amd64:v1.10.1": rpc error: code = Unknown desc = Error response from daemon: Get https://k8s.gcr.io/v2/: dial tcp 74.125.203.82:443: connect: connection timed out
Warning Failed 53s (x3 over 105s) kubelet, node01 Error: ErrImagePull
Normal BackOff 15s (x5 over 105s) kubelet, node01 Back-off pulling image "k8s.gcr.io/kubernetes-dashboard-amd64:v1.10.1"
Warning Failed 15s (x5 over 105s) kubelet, node01 Error: ImagePullBackOff
Normal Pulling 2s (x4 over 112s) kubelet, 01 Pulling image "k8s.gcr.io/kubernetes-dashboard-amd64:v1.10.1"
用手动下载的方法进行解决
# vim docker_install_dashboard.sh
#!/bin/sh
docker pull mirrorgooglecontainers/kubernetes-dashboard-amd64:v1.10.1
docker tag mirrorgooglecontainers/kubernetes-dashboard-amd64:v1.10.1 k8s.gcr.io/kubernetes-dashboard-amd64:v1.10.1
docker rmi mirrorgooglecontainers/kubernetes-dashboard-amd64:v1.10.1
# sh docker_install_dashboard.sh
然后再执行以下部署清单
kubectl apply -f https://raw.githubusercontent.com/kubernetes/dashboard/v1.10.1/src/deploy/recommended/kubernetes-dashboard.yaml
# kubectl get pods -n kube-system | grep dash
kubernetes-dashboard-5f7b999d65-fcb28 1/1 Running 0 71s
可以看到kubernetes-dashbroad 已经运行
默认服务暴露为ClusterIP类型的,我们需要将其改为NodePort 类型
# kubectl patch svc kubernetes-dashboard -p '{"spec":{"type":"NodePort"}}' -n kube-system
# kubectl get svc -n kube-system
\NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
kube-dns ClusterIP 10.96.0.10 <none> 53/UDP,53/TCP,9153/TCP 27d
kubernetes-dashboard NodePort 10.109.190.204 <none> 443:31984/TCP 3m41s
这个时候可以看到登录界面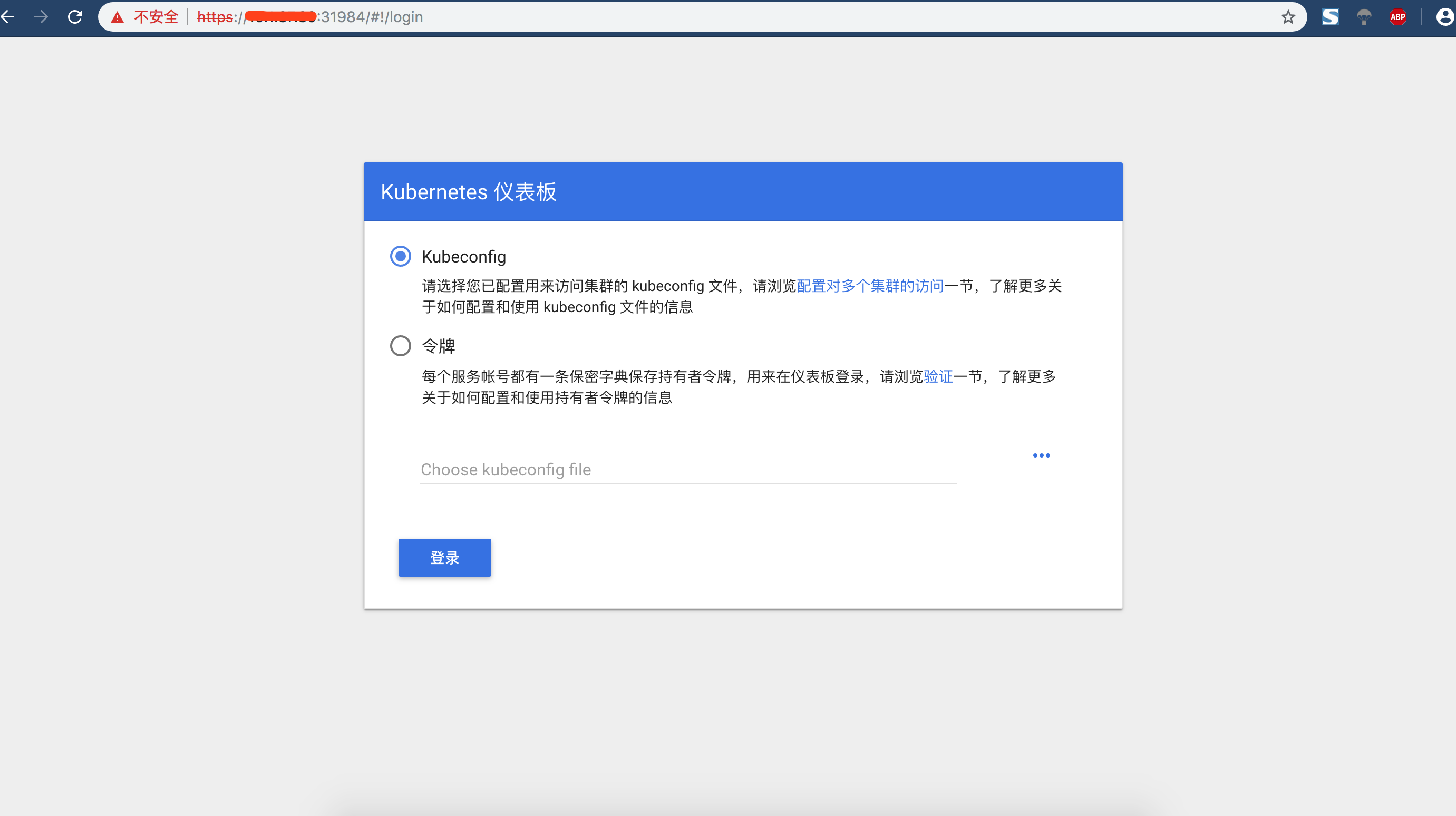
使用用token实现认证登录
这里登录需要的是serviceaccount用户, 所以这里创建 serviceaccount
# kubectl create serviceaccount dashboard-admin -n kube-system
serviceaccount/dashboard-admin created
# kubectl get sa -n kube-system | grep dash
dashboard-admin 1 6m33s
serviceaccount 创建好后, 需要将serviceaccount绑定cluster这个角色上
# kubectl create clusterrolebinding dashboard-cluster-admin --clusterrole=cluster-admin --serviceaccount=kube-system:dashboard-admin
clusterrolebinding.rbac.authorization.k8s.io/dashboard-cluster-admin created
# kubectl get secret -n kube-system | grep dash
dashboard-admin-token-grj84 kubernetes.io/service-account-token 3 5m46s
绑定好 cluster 后, 查看token信息,并拿token进行登录
# kubectl describe secret -n kube-system dashboard-admin-token-grj84
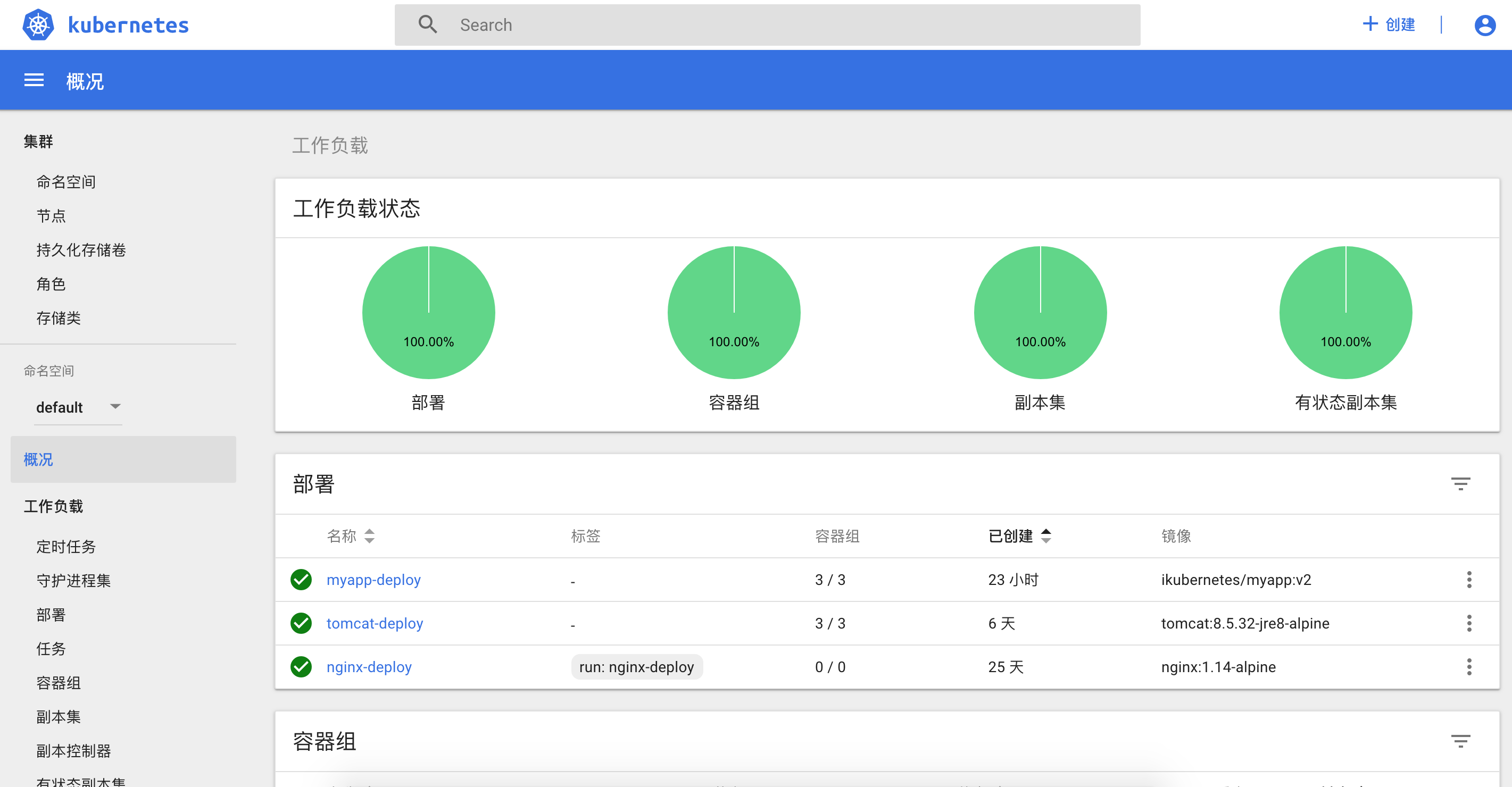
登录后,可以看到整个kubernetes集群的概况

建立专用dashborad用户
# cd /etc/kubernetes/pki/
# (umask 077; openssl genrsa -out dashboard.key 2048)
# openssl req -new -key dashboard.key -out dashboard.csr -subj "/O=ssjinyao/CN=dashboard"
# openssl x509 -req -in dashboard.csr -CA ca.crt -CAkey ca.key -CAcreateserial -out dashboard.crt -days 3650
Signature ok
subject=/O=ssjinyao/CN=dashboard
Getting CA Private Key
# kubectl create secret generic dashboard-cert -n kube-system --from-file=dashboard.crt=./dashboard.crt --from-file=dashboard.key=./dashboard.key
secret/dashboard-cert created
# kubectl create serviceaccount def-ns-admin -n default
serviceaccount/def-ns-admin created
role binding 到 default 名称空间,只允许访问default 名称空间
# kubectl create rolebinding def-ns-admin --clusterrole=admin --serviceaccount=default:def-ns-admin
rolebinding.rbac.authorization.k8s.io/def-ns-admin created
# kubectl describe secret admin-token-hxqqf # 查看 token信息登录
接下来配置kube config 文件认证
# kubectl config set-cluster kubernetes --certificate-authority=./ca.crt --server="https://10.1.87.80:6443" --embed-certs=true --kubeconfig=/root/def-ns-admin.conf
Cluster "kubernetes" set.
# kubectl config view --kubeconfig=/root/def-ns-admin.conf
apiVersion: v1
clusters:
- cluster:
certificate-authority-data: DATA+OMITTED
server: https://10.1.87.80:6443
name: kubernetes
contexts: []
current-context: ""
kind: Config
preferences: {}
users: []
# CLUSTER_ADMIN_TOKEN=$(kubectl get secret -n kube-system dashboard-admin-token-grj84 -o jsonpath={.data.token} | base64 -d )
# kubectl config set-credentials dashboard-cluster-admin --token=$CLUSTER_ADMIN_TOKEN --kubeconfig=/root/def-ns-admin.conf
User "dashboard-cluster-admin" set.
# kubectl config set-context dashboard-cluster-admin@kubernetes --cluster=kubernetes --user=dashboard-cluster-admin --kubeconfig=/root/def-ns-admin.conf
# kubectl config use-context dashboard-cluster-admin@kubernetes --kubeconfig=/root/def-ns-admin.conf
将生成的conf文件远程复制到桌面上
ssjinyao ➤ scp root@10.1.87.80:/root/def-ns-admin.conf ~/Desktop
此时使用可以用 kubeconfig 来登录dashboard 了